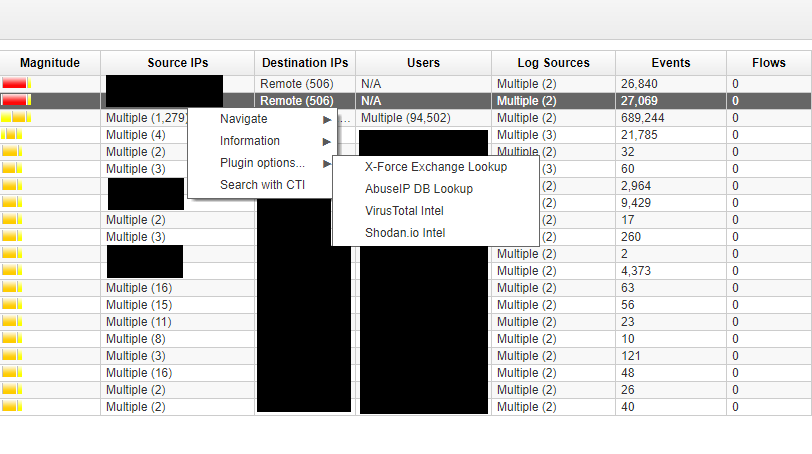
Sensors | Free Full-Text | Teaching and Learning IoT Cybersecurity and Vulnerability Assessment with Shodan through Practical Use Cases
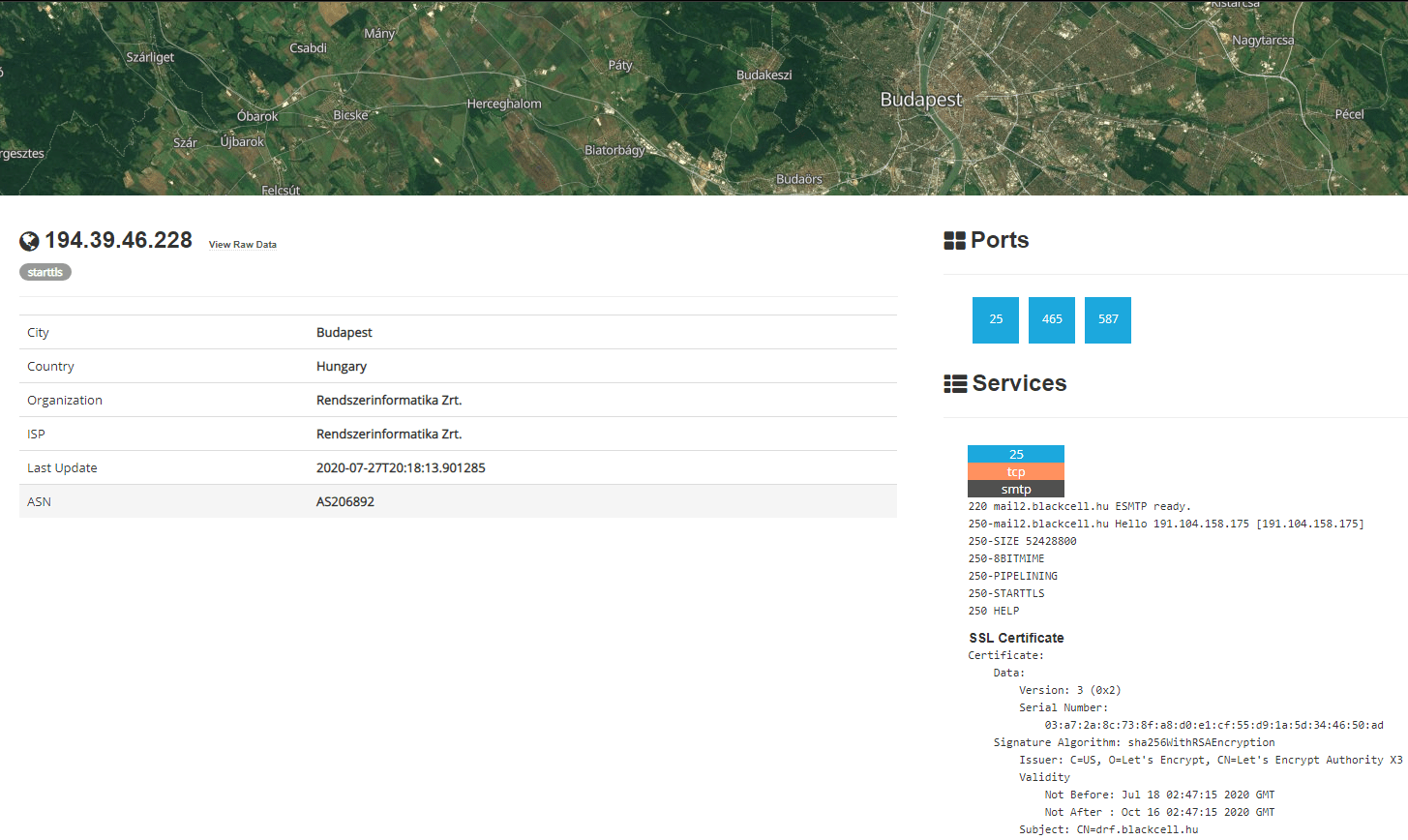
Sensors | Free Full-Text | Teaching and Learning IoT Cybersecurity and Vulnerability Assessment with Shodan through Practical Use Cases

Shodan founder John Matherly on IoT security, dual-purpose hacking tools, and information overload | The Daily Swig
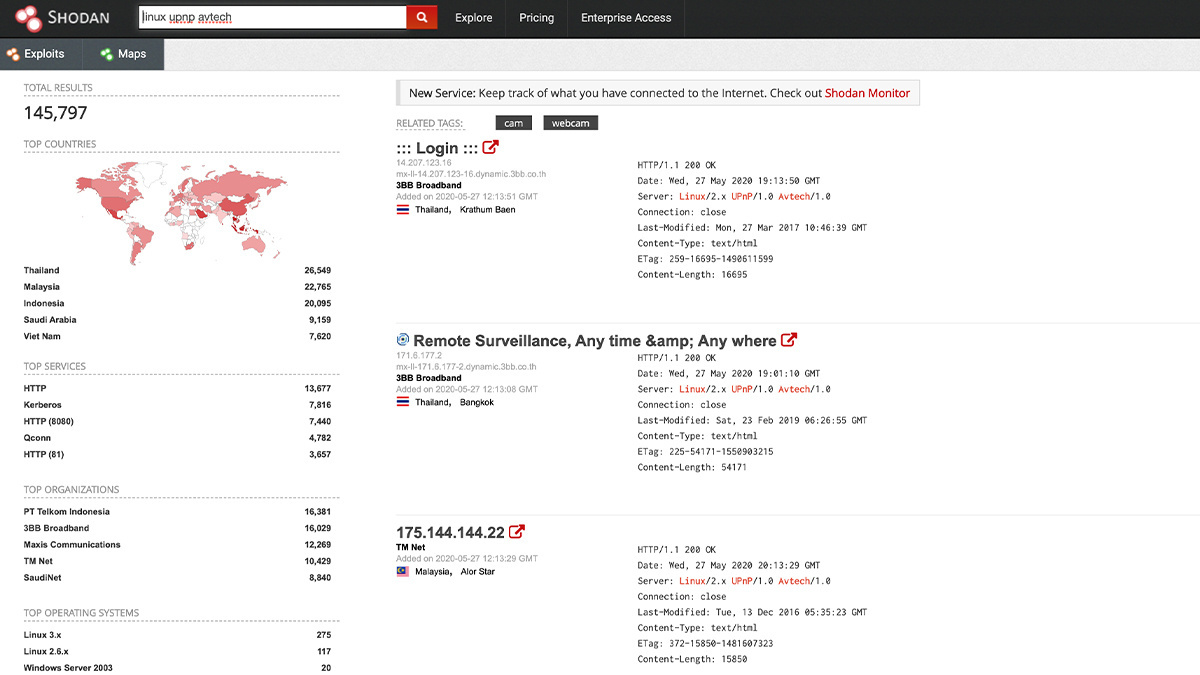
Shodan founder John Matherly on IoT security, dual-purpose hacking tools, and information overload | The Daily Swig
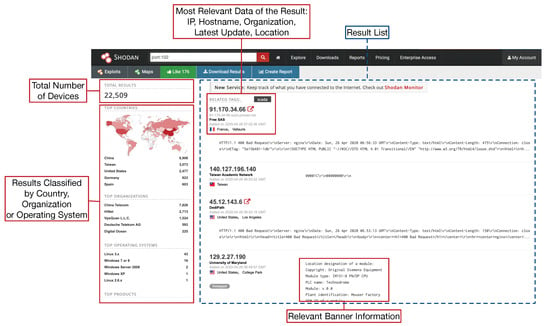
Applied Sciences | Free Full-Text | Use Case Based Blended Teaching of IIoT Cybersecurity in the Industry 4.0 Era


![Shodan, How to Avoid your Webcam and IoT devices from Being Hacked [Updated] - Shodan, How to Avoid your Webcam and IoT devices from Being Hacked [Updated] -](https://santandergto.com/wp-content/uploads/2019/06/shodan-explore-unsecured-webcams.jpg)



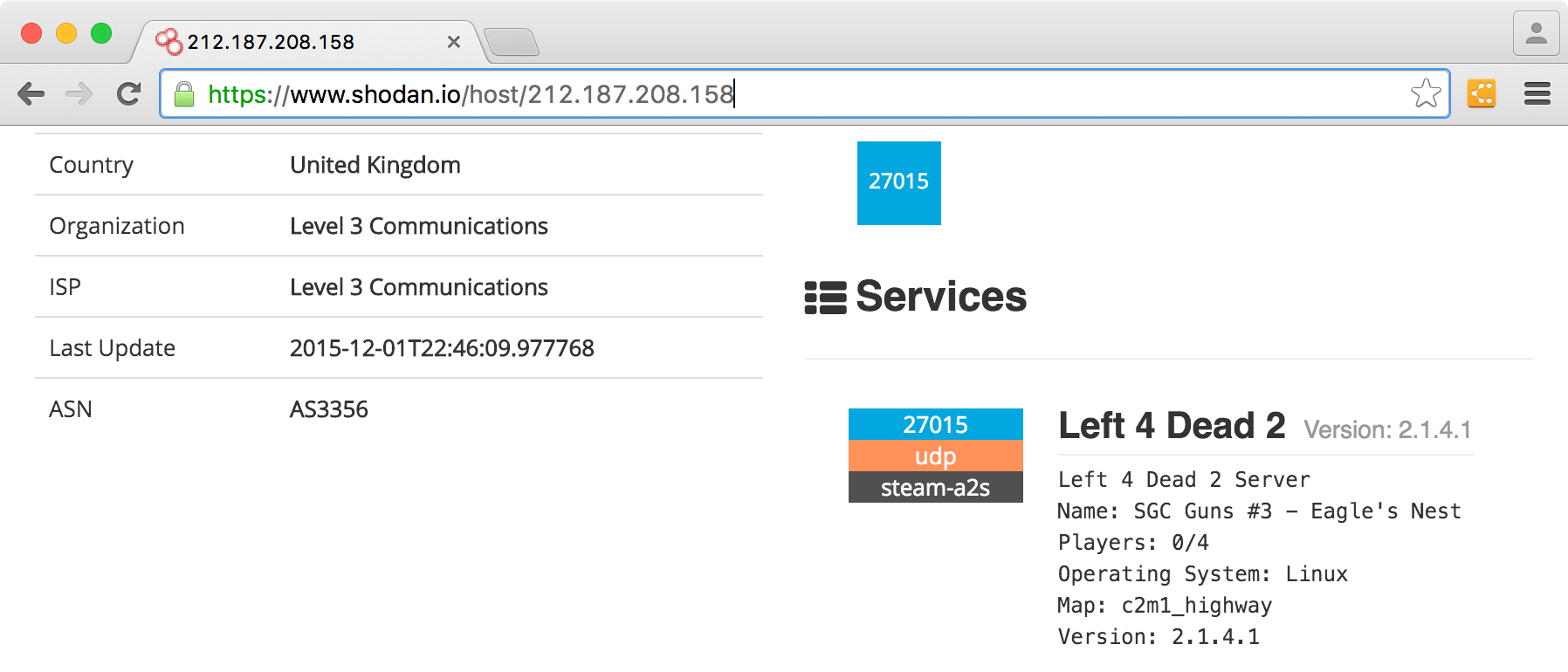


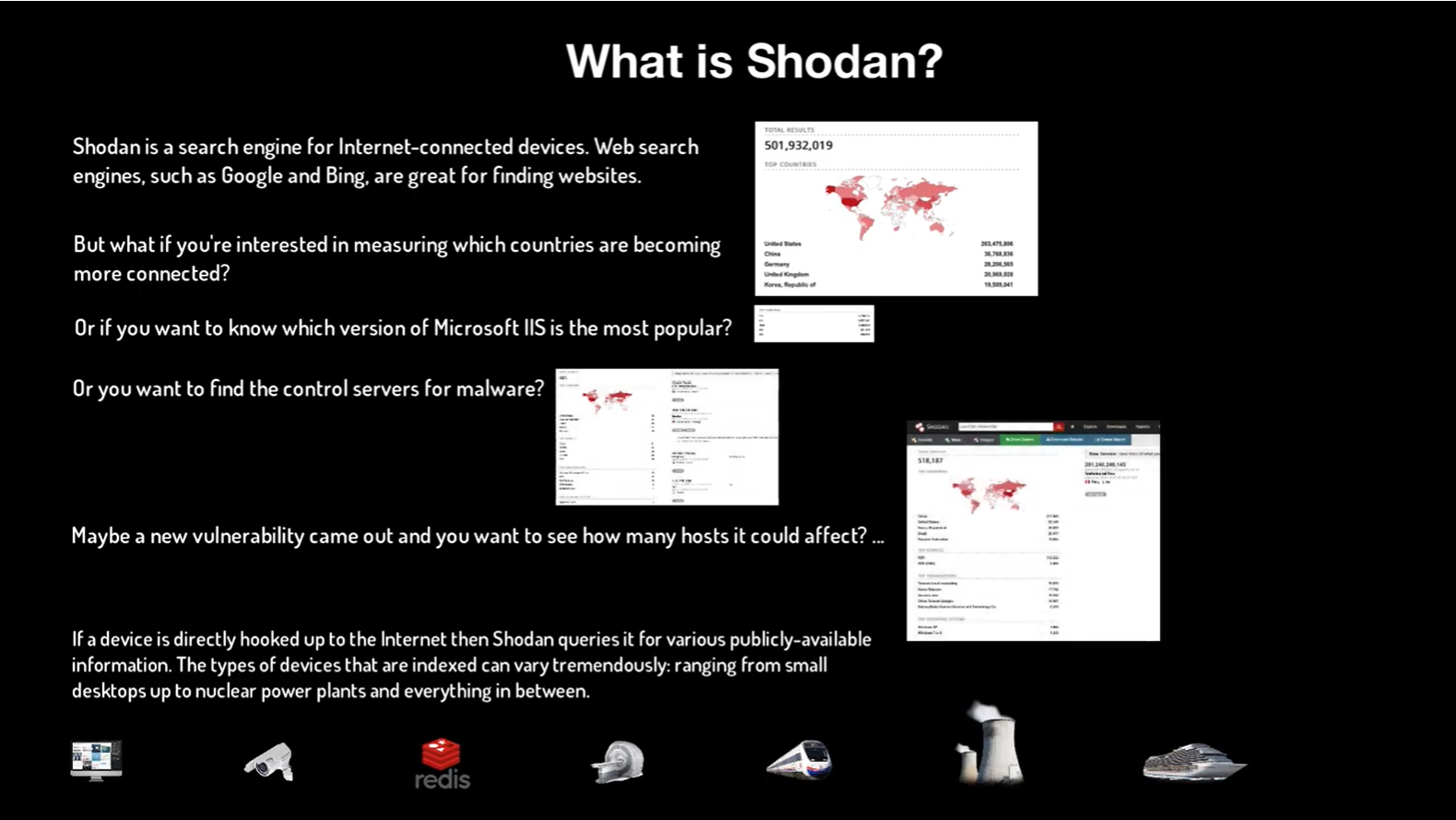

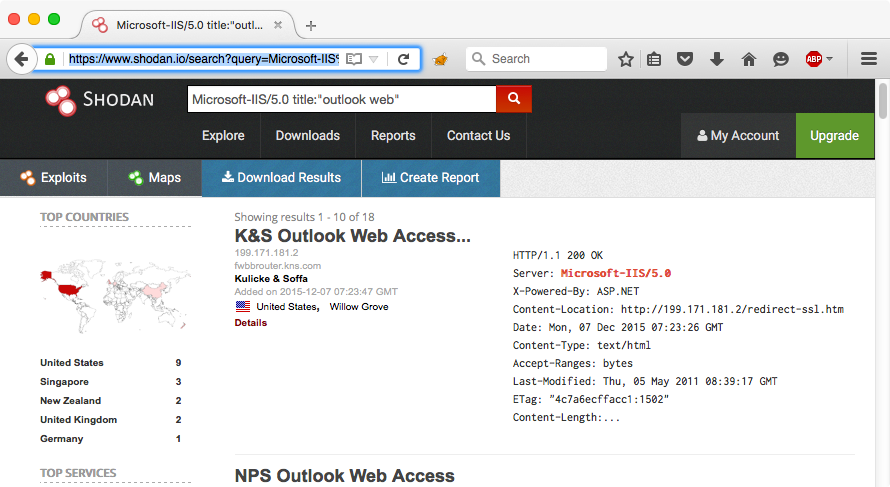

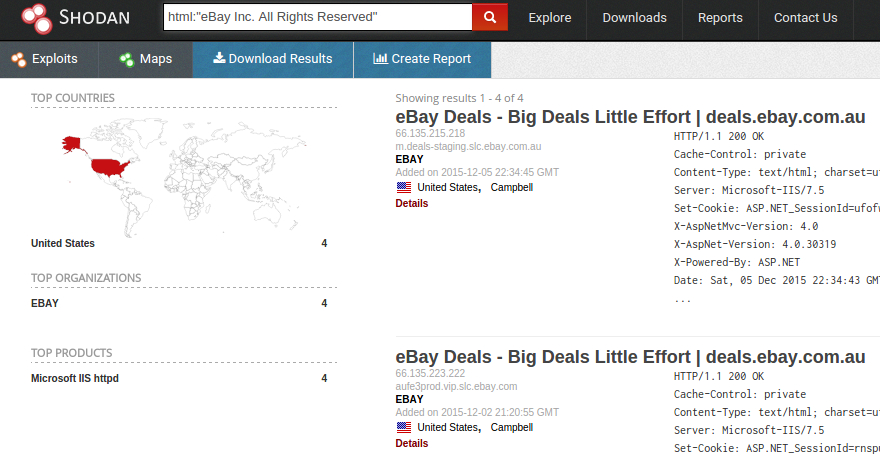
![Shodan, How to Avoid your Webcam and IoT devices from Being Hacked [Updated] - Shodan, How to Avoid your Webcam and IoT devices from Being Hacked [Updated] -](https://santandergto.com/wp-content/uploads/2019/06/shodan-website.jpg)